Dreamers aren't the only ones with their heads in the clouds anymore. Whether it's a business calendar, banking information or pictures from Junior's bar mitzvah, more and more of the information, documentation and other stuff we access every day is stored up among those puffy white swaths of cotton in the sky, figuratively speaking. Many of us just don't seem to know it. In a recent poll, more than 50 percent of respondents said they hardly or never used cloud computing services. Yet, 95 percent said they regularly used Facebook, Gmail, GoogleDocs, all of which are popular cloud-based networks [source: Citrix].
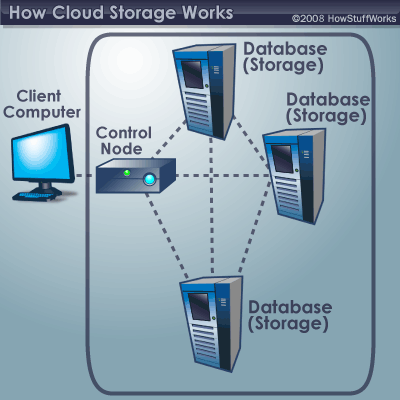
Generally, the "cloud" refers to any network used to store, access and share data using internet-connected devices. Consider, for example, the way many of us look at photos. You take a shot with digital camera, download it to your laptop and then upload it to your favorite photo hosting site, such as Flickr. Once the photo is up, you can then access it with other internet-connected devices like a cell phone, tablet, or even those relics of our recent, plugged-in past, the desktop computer. This is the cloud.
Advertisement
There are two types of cloud networks: public, which covers all the information you share with the world in a cloud service offered to everyone, like Facebook; and private, a unique network developed by the user or a cloud service provider, such as Amazon's Virtual Private Cloud, concerning the stuff you keep to yourself, or perhaps share with some friends. Like miniature versions of Facebook and Tumblr, groups of users will eventually be able to form their own social networks with their own privacy settings [source: Tadjer].
The cloud computing model allows users to access just about all the data (and other stuff) they could possibly need with a couple of key strokes. Or less. Experts say that predictive technology will ultimately give devices the power to foresee where you are going and the cloud-stored stuff you might want to access when you get there [source: Tadjer].
That sounds useful. Also a little creepy. So is the cloud safe? Read on to find out.
Advertisement