When a computational problem is really complex, it can take a single computer a long time to process it — millions of days, in some cases. Even supercomputers have processing limitations. Distributed computing systems, fortunately, can be deployed to handle complex computational tasks efficiently.
Imagine you've been assigned the task of pushing a very heavy car up a hill. You're allowed to recruit people who aren't doing anything else to help you move the car. You've got two choices: You can look around for one person big and strong enough to do it all by themself or you can grab several average people to push together. Most of the time, it'll be easier to gather a group of average-sized people. It might sound strange but distributed computer systems use the same principle.
Advertisement
Distributed computing is an affordable alternative to high-performance computing. While high-performance computing uses supercomputers, distributed computing leverages many computers networked together. It's more scalable and taps into resource pooling.
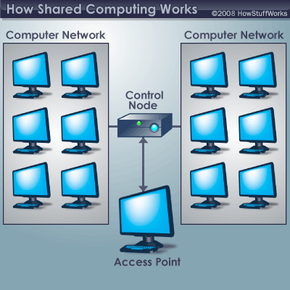
A distributed computing system is a network of computers that work together to accomplish a specific task. Each computer donates part of its processing power — and sometimes other resources — to help achieve a goal. By networking thousands of computers together, a distributed computing system can equal or even surpass the processing power of a supercomputer.
Most of the time, your computer isn't using all of its computational resources. There are other times when you might have your computer on, but aren't actually using it. A distributed computing system, also called a shared computing system, takes advantage of these resources that otherwise would remain unused.
Shared computing systems are great for certain complex problems, but aren't useful for others. They can be complicated to design and administer. While several computer scientists are working on a way to standardize shared computing systems, many existing systems rely on unique hardware, software and architecture.
What pieces make up a typical distributed computing system? Keep reading to find out.
Advertisement