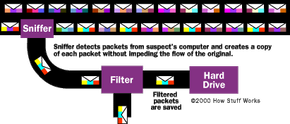
Computer network administrators have used packet sniffers for years to monitor their networks and perform diagnostic tests or troubleshoot problems. Essentially, a packet sniffer is a program that can see all of the information passing over the network it is connected to. As data streams back and forth on the network, the program looks at, or "sniffs," each packet.
Normally, a computer only looks at packets addressed to it and ignores the rest of the traffic on the network. When a packet sniffer is set up on a computer, the sniffer's network interface is set to promiscuous mode. This means that it is looking at everything that comes through. The amount of traffic largely depends on the location of the computer in the network. A client system out on an isolated branch of the network sees only a small segment of the network traffic, while the main domain server sees almost all of it.
A packet sniffer can usually be set up in one of two ways:
- Unfiltered - Captures all of the packets
- Filtered - Captures only those packets containing specific data elements
Packets that contain targeted data are copied as they pass through. The program stores the copies in memory or on a hard drive, depending on the program's configuration. These copies can then be analyzed carefully for specific information or patterns.
When you connect to the Internet, you are joining a network maintained by your ISP. The ISP's network communicates with other networks maintained by other ISPs to form the foundation of the Internet. A packet sniffer located at one of the servers of your ISP would potentially be able to monitor all of your online activities, such as:
- Which Web sites you visit
- What you look at on the site
- Whom you send e-mail to
- What's in the e-mail you send
- What you download from a site
- What streaming events you use, such as audio, video and Internet telephony
- Who visits your site (if you have a Web site)
In fact, many ISPs use packet sniffers as diagnostic tools. Also, a lot of ISPs maintain copies of data, such as e-mail, as part of their back-up systems. Carnivore and its sister programs were a controversial step forward for the FBI, but they were not new technology.