Computer Security Systems
Computer security is an increasingly important consideration. From authentication to encryption keys, learn how to keep your computer's hard drive protected and your personal information safe.
Learn More
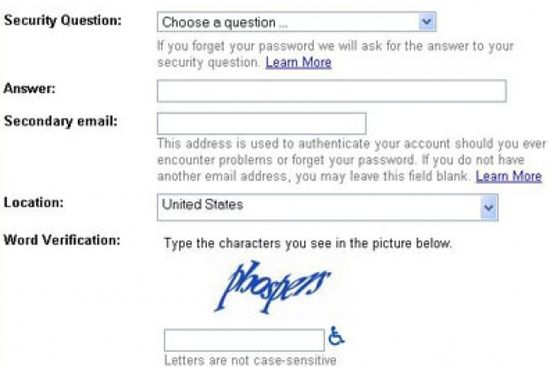
In the modern day, people have to try and stay organized with dozens, maybe even hundreds, of online accounts. As a result, they may fall back using easy-to-guess passwords out of a misguided sense of convenience, or using the same password across multiple sites.
By Talon Homer
In a world where digital privacy is increasingly important, finding the right tools to protect your data is essential. With mobile phones becoming central to our lives, it's crucial to choose apps that prioritize privacy.
In today's digital age, safeguarding your mobile privacy is vital. Here are three easy steps, powered by Startpage, to keep your digital life secure.
Advertisement
In the realm of online privacy, private search engines provide a shield against intrusive tracking and data collection. Let's explore five prominent options.
In the digital world, alphanumeric characters play an important role. The term "alphanumeric" encompasses both letters and numbers, creating a versatile set that forms the foundation of written language, computer programming and secure password creation.
By Yara Simón
Websites like Spokeo, PeopleFinder and Intelius collect reams of data on you, your relatives, court records and other personal information. But getting it removed isn't so easy.
By Dave Roos
Do you have a password manager? How about a VPN? Here's why you might want both, in the form of antivirus software, available with a discount from HowStuffWorks.
Advertisement
Private browsers and search engines offer much more protection than using a regular browser or search engine, or a browser with privacy mode-enabled. They can shield your sensitive data, ward off third-party ads and trackers, and provide a safer browsing experience.
We're told to change our computer passwords often, but sometimes it can be a hassle to remember how to do it. Here are some easy instructions for changing your Gmail password.
By Jeremy Glass
Some Airbnb guests have found hidden cameras in their rented homes. Is this legal? And how can you tell if you're being spied on?
It may seem like you get endless alerts to update your Microsoft Windows system and you might be tempted to skip a few updates. Is there any harm in doing that?
Advertisement
Zoom bombing - when intruders hijack your videoconference calls or virtual learning sessions - has become a big deal. But how do you stop it?
What really happens when you transfer your browser to the incognito feature? You may think you're completely anonymous on the internet, but that's not what's happening.
Even if you use the "incognito" setting on your browser, your personal and search data are still being collected at an alarming rate. Private search engines and browsers aim to lessen your digital footprint.
By Dave Roos
To what extent is U.S. intelligence able to conduct surveillance on the internet activity and electronic communications of U.S. citizens?
Advertisement
Data privacy concerns have prompted some new laws to go into effect in the European Union - and that means changes for consumers in the rest of the world too.
By Dave Roos
HowStuffWorks explains how blockchain technology, which relies upon a shared record of transactions across a peer-to-peer network of computers, is taking over the world.
It's the technology behind the meteorically rising bitcoin, and it could be really, really big.
The guys at Stuff They Don't Want You To Know talk about whether you can really delete your internet history - and why you want to.
By Diana Brown
Advertisement
It's sweet to have a personal assistant like Amazon's Alexa do your bidding. Except when it does something you didn't anticipate, like order an adorable dollhouse.
Trolls are everywhere these days, driving people off Twitter and wreaking havoc online. They also have specific personality traits that the general population doesn't.
By Julia Layton
And the FBI already has said it'll help other law enforcement agencies with locked phones.
By John Donovan
Advertisement
Whether you applaud their Robin Hood-style ideology of championing free speech or detest their reckless disregard for the consequences of their actions, it's undeniable that Anonymous has become a force to be reckoned with in recent years. From hacking politicians' emails to taking down government websites, many of the group's actions seem to straddle the line [...] The post 9 Things Everyone Should Know About The Hacktivist Group Anonymous appeared first on Goliath.
By Wes Walcott
The short answer is yes. The long answer? Some people do it for mischief, others for criminal purpose, and even governments are in on the game.
By Chris Opfer