Computer & Internet Security
Computer surveillance and security covers a wide range of ways to keep you and your information safe. Learn about firewalls, zombie computers, hackers and workplace surveillance.
Learn More / Page 3
Internet censors range from parents and employers to national governments. They block access to the Web pages they identify as undesirable.
E-mail scams are often well-disguised and can be very dangerous. Check out some examples of e-mail scams in this article.
By Tim Crosby
Without hackers, we'd have no PCs or iPods. Yet, hackers have gotten a bad reputation as criminals of the computer age. Are they friends or foes?
Advertisement
As the famous cartoon has it, "On the internet, nobody knows you're a dog." Online fraud is one of the fastest-growing crimes -- so how can you protect yourself?
By Joe Wallace
With the evolution of the internet, the big kid in class who used to steal your lunch money now hacks your e-mail, sends you threatening messages, and sabotages your computer. If you're wondering how to stop cyberbullying, read on!
When hackers take over computers to do their Internet bidding, they create zombie computers. Allegedly, one hacker under investigation used a single computer to control a network of more than 1.5 million zombie computers.
In "Live Free or Die Hard," Detective John McLane fights a group that carries out attacks using the Internet. Is it really possible for hackers to cause economic or physical devastation in the United States?
Advertisement
How did hackers exploit four different "zero day" flaws in Microsoft Word? Find out what went wrong with Microsoft Word.
By Julia Layton
Logic bombs can cripple a company's computer system and either reveal or destroy sensitive information. It's often a tool used by angry employees -- in the IT world, it has a reputation of being associated with "disgruntled employee syndrome."
By Julia Layton
Most people associate phishing with e-mail messages imitating banks or other businesses in an attempt to scam victims into revealing personal information. But e-mail messages are only one small piece of a phishing scam.
According to recent estimates, more than two-thirds of all PCs are infected with some kind of spyware. These programs track your Web habits and more. Is your computer doomed, or can you get rid of spyware?
By Dave Coustan
Advertisement
If you're surfing the Internet at work, you may not be the only one who knows. Watching workers has become an industry unto itself. Find out exactly how companies are monitoring employees.
By Kevin Bonsor
If George Orwell's book "1984" creeped you out, you'll want to read the facts about the FBI's Operation Carnivore. It gave agents the permission and technology to access to the online and e-mail activities of suspected criminals.
By Jeff Tyson
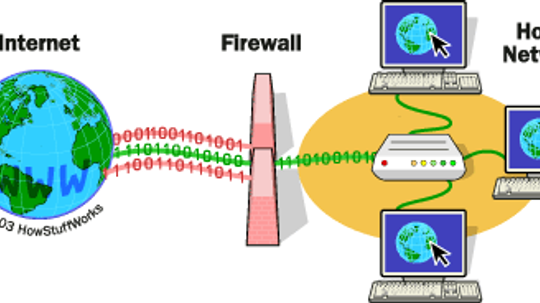
Firewalls have helped protect computers in large companies for years. Now they're a critical component of home networks as well. What are they protecting you from?
By Jeff Tyson
Cookies are widely used by Web sites to keep track of their visitors, but they can also provide a better user experience. Are cookies letting Big Brother into your PC?
Advertisement
Both BO and Netbus are Windows 95/98 applications designed to allow other people to access your machine over the Internet. But here's the kicker - you're the one installing it!
From Trojan horses, to worms and viruses, we give you the skinny on how viruses can infect your system through email.
Fortunately the Year 2038 problem is somewhat easier to fix than Y2K on mainframes. Learn about the standard time library and how C programming is involved with this computer blunder.
Computer viruses range from pesky to outright dangerous. Some just display a message, while others erase your entire hard disk. Clicking on what looks like a harmless e-mail message can lead to hours of recovery efforts, if not irreparable damage.
Advertisement
Until recently, computer programmers used two-digit placeholders for the year portion of the date in their software. Guess what happened when we realized the system couldn't account for the first two numbers? Mass panic.